An introduction to security management is covered in this article on Bluetooth SMP Security Management. Here is a detailed method of pairing BLE Security Management (SM).
At the beginning of the pairing process, the first phase is the matching feature of the two parties. If one party does not support pairing, then the pairing will not be performed. If both pairs are supported, then the appropriate method will be selected for pairing.
Pairing feature
First look at what the content of this pairing feature is (the first three will determine the key generation method for pairing the second stage):
- IO capability;
- OOB;
- authenTIcaTIon requirements;
- key size;
- key distribute.
Key generated in pairing
LE legacy pairing
Temporary Key (TK): a short-lived Key, 128-bit, used to generate STK;
Short Term Key (STK): 128-bit, which will be used to encrypt the paired link.
LE Secure ConnecTIons
Long Term Key (LTK): 128-bit, which will be used to encrypt the paired link.
authenTIcation
The authentication requirements are set by GAP, mainly for the Bond type and MITM (man-in-the-middle) requirements.
Key distribute
For key distribute, the Initiator first sends its own request to the Responder, indicating which Keys you want to send, and which Keys you want to send. After the Responder receives it, it will reply to the Key that the final parties can distribute. This level of negotiation is two steps, which is relatively simple.
Security attribute - Security Properties
Divided into the following types of security attributes:
- LE Secure Connections pairing (supported by BT4.2);
- Authenticated MITM protection (someone involved in the security of interference, can be a person to enter a password, or obtain a password through OOB, also supports digital comparison for Secure Connections);
- Unauthenticated no MITM protection;
- No security requirements;
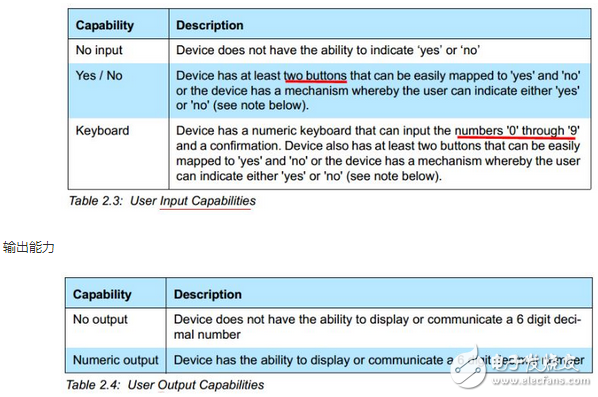
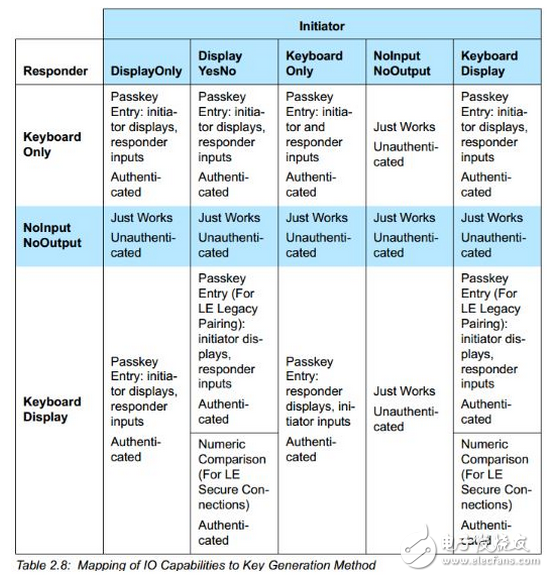
IO capabilities
Indicates the ability to input and output. The input is a button, a keyboard, and the output is an interface for displaying numbers.
Input ability
Combination of input and output
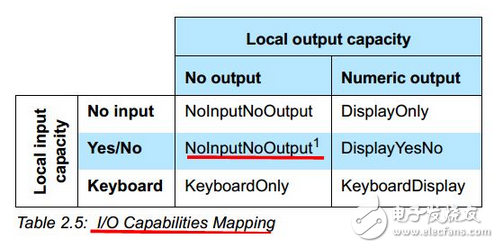
OOB Authentication Data
OOB Auth Data is a device that holds the peer's data and is used to authenticate the peer device.
- LE legacy pairing: Use the OOB method to hold the OOB Auth Data on both ends;
- LE Secure Connections pairing: The OOB method can be used by holding OOB Auth Data on at least one end.
Encryption Key Size
The encryption Key Size is between 7 and 16 bytes;
The devices at both ends should select the smaller one of the max key len of each other;
Both ends of the device should detect whether the max key len is less than its own min key len. If it is less than the pair, the pair fails.
The generated key to the final key may be cropped. The key generation is a 16 byte key value, but when the max key len is less than 16, then it is reduced to a smaller result key and then distributed.
Pairing algorithm
After the pairing feature is exchanged in the first phase, these feature content will be used to select which Key generation method to use.
For example, the generation of Temperary Key: such as Just Works, Passkey Entry, OOB can be used to generate TK, just to see if the device has this capability.
Select the method of Key generation
If there is no MITM in auth Req, it means that no one needs to participate in the middle, so IO capabilities will be ignored, and only Just Works will be OK.
If there is OOB data, auth Req will be directly ignored, and the way of OOB will be directly selected.
Legacy pairing generates STK
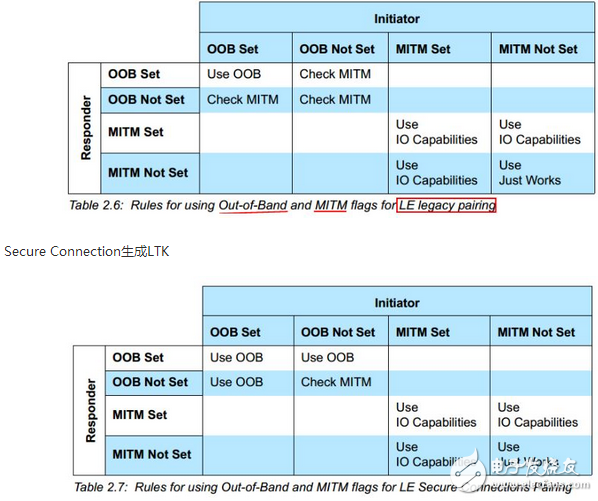
Specific algorithm corresponding to Use IO capabilities
In the above two figures, there is a Use IO capabilities item. In fact, this item has subdivisions:
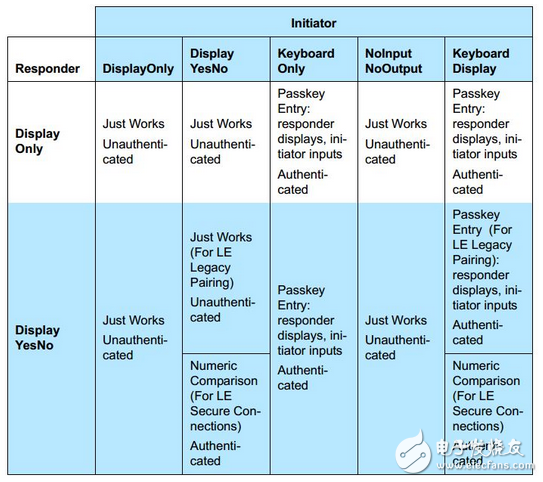
LE Legacy Pairing - Just Works
The Just Works method does not protect against eavesdroppers and man-in-the-middle attacks. It is only attacked during the pairing process, and the data transmission of the encrypted link is trusted. The security level is very low.
LE Legacy Pairing - Passkey Entry
This method is paired by inputting a 6-digit number to generate an STK. The 6-digit number is a randomly generated value between 000000 and 999999. This value is equivalent to a TK. For example, if the remote end displays this number, you need to input this number to the local device to pair with the remote device. If you enter 019655, then the temporary Key–TK at this time is: 0x00000000000000000000000000004CC7.
Out of Band
This method is to obtain the OOB data through other means on the device other than BLE, such as IR IR, or the rest, so the data transmission is invisible to the Bluetooth eavesdropper/attacker. Therefore, it will appear to be safer.
LE Legacy Pairing Phase II
That is the generation of STK, this part can be briefly described as the implementation of the following steps:
1. The Initiator generates a 128-bit random number, Mrand, and uses this Mrand in conjunction with some other input to calculate a 128-bit Mconfirm value using c1 in the Password Toolbox:
Mconfirm = c1(TK, Mrand,
Pairing Request command, Pairing Response command,
Initiating device address type, initiating device address,
Responding device address type, responding device address)
The Responder also generates a 128-bit random number Srand, and uses this Srand in conjunction with some other input to calculate a 128-bit Sconfirm value using c1 in the password toolbox:
Sconfirm = c1(TK, Srand,
Pairing Request command, Pairing Response command,
Initiating device address type, initiating device address,
Responding device address type, responding device address)
The Initiator then sends its calculated Mconfirm value to the Responder via the Pairing Confirm packet, and the Responder also sends its calculated Sconfirm value to the Initiator via the Pairing Confirm packet.
After receiving the Sconfirm, the Initiator sends the Mrand value to the Responder through the Pairing Random packet.
After receiving the Mrand value, the Responder calculates its Mconfirm value and compares it with the Mconfirm value sent by the previous Initiator. If the difference indicates that the pairing failed. If they are the same, the Responder will also send its Srand value to the Initiator through the Pairing Random package;
The Initiator also calculates the Sconfirm value of the received Srand value and compares it with the Sconfirm value sent by the previous Responder. If the pairing fails, the pairing fails. If the same, continue;
The Initiator calculates the STK and notifies its Controller to allow link encryption:
STK = s1(TK, Srand, Mrand)
Throughout the above processes, in fact, the two send a 128-bit random number to generate STK. As long as the eavesdropper or attacker knows TK, this step is very easy to crack.
The second stage of LE Secure Connections
That is to say, the generation of LTK is much more complicated than Legacy pairing, which is why BT 4.2 is much safer. This section is only a brief description of the content, the detailed process needs to be compared to Spec's flow chart.
Public Key exchange
Authentication Phase 1-Just Works or Numeric Comparison
Authentication phase 1-Passkey Entry mode
Authentication Phase 1-Out of Band Mode
Authentication Phase 2 and LTK Computing
BR/EDR, LE Cross Key Reference
This part refers to the Bluetooth dual-mode device, and supports Secure Connections. The pairing keys can be shared with each other, so that some duplicate pairs can be omitted, but the Key also has a conversion algorithm, that is, h6 in the password toolbox.
Office Lighting Led Driver
A comprehensive series of Office lightings drivers, suitable for use in a range of Office Lighting applications, including meeting room Lighting, Production line Lighting, Medical Lighting, Transportation Lighting, Entertainment Lighting, etc. We have skilled engineers to answer all your questions and enquiries and provide all-round solutions basis on your project(s) and provide technical supporting.
Specifically for office lighting, Generally used in the panel more, instead of the traditional lamp, but no flicker power, long hours of office work on the great damage to the glasses. Power requirements are not waterproof, high PF value, long life.
Input voltage: 100-277vac / 100-240vac / 100-130vac / 180-240vac / 100-347V
output voltage: 25-40vdc / 27-42vdc / 35-45vdc / 50-70vdc / 12Vdc / 24vdc
current: 100mA-8000mA.
Power factor: >0.9
Dimming:0-10V / PWM / RX / DALI.
>=50000hours, 3-5 years warranty.
certificate: UL CE FCC TUV SAA ect.

What's the benefits of Fahold Driver?
- Standard Linear Lighting
- Cost-effective led driver solution for industry,commercial and other applications
- Good quality of led driver with high efficiency output to meet different requirements
- Easy to order and install,requiring less time,reducing packaging waste and complexity
- Flexible solution
FAQ:
Question 1:Are you a factory or a trading company?
Answer: We are a factory.
Question 2: Payment term?
Answer: 30% TT deposit + 70% TT before shipment,50% TT deposit + 50% LC balance, Flexible payment
can be negotiated.
Question 3: What's the main business of Fahold?
Answer: Fahold focused on LED controllers and dimmers from 2010. We have 28 engineers who dedicated themselves to researching and developing LED controlling and dimming system.
Question 4: What Fahold will do if we have problems after receiving your products?
Answer: Our products have been strictly inspected before shipping. Once you receive the products you are not satisfied, please feel free to contact us in time, we will do our best to solve any of your problems with our good after-sale service.
48W Led Driver,Led Driver 700Ma,Led Dimming Driver
ShenZhen Fahold Electronic Limited , https://www.fahold.com